Our cybersecurity framework is designed with Small and Medium Organizations in mind.
The Canadian Cybersecurity Skills Framework can be adapted to SMEs. Within cybersecurity, most small and medium enterprises (SMEs) have the following characteristics:
- There are rarely any cybersecurity specialists on hand
- They are not typically resourced for full-time cyber staff
- Design/Develop roles are either outsourced or systems/applications are acquired ‘off-the-shelf’
- Individuals will often fill multiple roles that include cybersecurity tasks.
Consequently, when organizations look at the U.S. NICE Framework it may be overwhelming. However, there is the potential to identify scenarios or present examples that will help SMEs scale the U.S. NICE Framework using the Canadian Cybersecurity Skills Framework and this will also help define role-based knowledge, skills and abilities that will support cybersecurity within organizations.
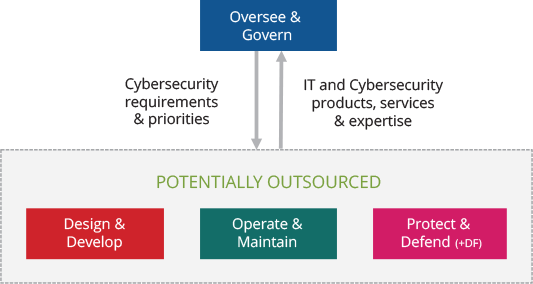
The graphic below provides an example of functions/tasks that the security generalist may perform from each of the work categories.
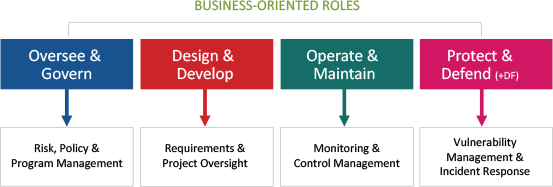
Security Generalist – Common Tasks & KSAs
Underpinning effectiveness in security generalist roles are basic knowledge, skills and abilities (KSAs) needed to support decision making and action. However, it is unlikely that they will have any extensive cybersecurity training or education. Accordingly, they should be offered sufficient learning opportunities to attain the required KSAs commensurate with their responsibilities as well as the threat, technical and business context. As shown in the figure below, this typically requires competencies and basic KSAs borrowed from some of the work roles within each major work category.
Common tasks:
- Assess the organization’s cybersecurity posture
- Facilitate identification of organizational cyber risks
- Identify non-technical cybersecurity controls
- Identify and liaise with technical experts, internal or external, on technical controls
- Develop organizational cybersecurity plans and policies
- Advise leadership on security awareness and training
- Monitor and support technical experts, whether in-house or outsourced, in their cybersecurity functions
- Coordinate cybersecurity incident response
- Monitor and report on response and mitigation actions and recommend courses of action based on technical advice
- Coordinate post-mortem activities on events and incidents, integrating lessons learned into organizational policies and procedures
Basic Knowledge:
- Technical context (e.g. organizational IT infrastructure, software, devices and policies)
- Cyber threat context (including deliberate, accidental, natural hazards)
- Business context (priorities, objectives, market, trends)
- Legal, policy and ethical context for security
- Cybersecurity risk management as part of organizational risk
- Cybersecurity incident management (domain specific)
- Cybersecurity processes, technology, trends and emerging issues
- Sources of cyber security expertise and resources
Basic Skills and Abilities:
- Providing business advice within the legal and policy cybersecurity context
- Exercising foresight and security planning to support digital business activities and growth
- Translating cyber risk to corporate risk
- Differentiating between compliance and risk
- Interpreting threat and risk assessments for the business context
- Assessing effectiveness of security controls against organizational security objectives
Adapting the Canadian Cybersecurity Skills Framework to Small and Medium Organizations
Example 1 – Medium sized organization with some in-house IT staff
In this example, there remains technical expertise in-house, but several cybersecurity roles are assumed by those who have other functions and are typically not cybersecurity specialists or may have only a small IT section who will be responsible for detection and incident response. In this example, the CIO would lead the small IT team and assume responsibilities for the technical aspects of the cybersecurity program while the C-suite representatives would remain responsible for defining the business priorities and risk landscape. For all Protect & Defend functions, they would likely be assumed by the IT team with specialized activities outsourced to a third party.
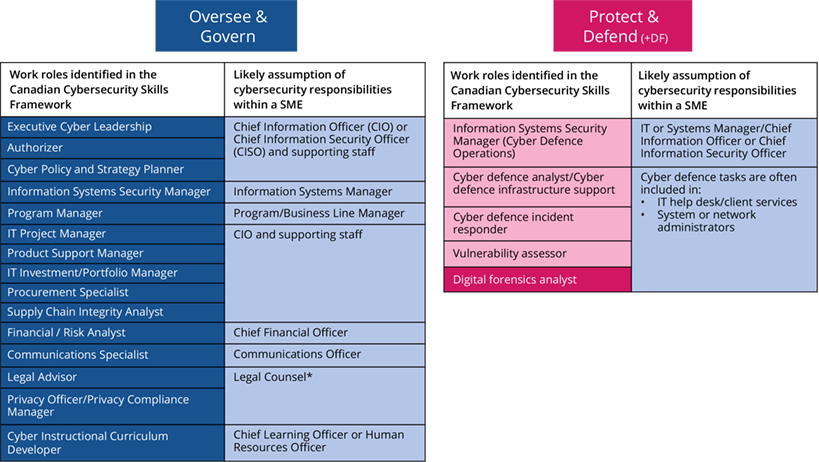
Example 2 – Small organization with limited IT dependence and no IT staff
In this example, the majority of technical work roles would be outsourced, but the primary ‘Oversee & Govern’ cybersecurity functions would remain within the organization. This individual would effectively be fulfilling the role of the ‘security generalist’.